Just like how keeping a safe in your home to protect your treasure or sensitive information is a part of prepping, so too is protecting yourself in the digital world. You wouldn’t tolerate someone sitting outside your bedroom window spying on you, so why tolerate the digital (and far more consequential) equivalent?
There are four major areas of concern:
- The data you have stored on your local devices, such as a phone, computer, or security system.
- How the devices you’ve brought into your life (eg. doorbell cameras or Alexas) can be used against you.
- Your data in the cloud, on machines outside of your physical control, such as your Gmail account or financial info.
- The connections that send data between your local stuff and the internet.
Attackers can hurt you through any one of those three areas. It might be a data breach due to poor corporate security, a government spying on you, or simply too much of your personal info being used in ways you don’t want it to be.

- Understand what "the cloud" means
- Don't use plain text messaging
- Most phone/video apps are insecure
- Use physical barriers to cover cameras and microphones
- Switch to internet browsers that respect privacy/security
- Block trackers with browser plugins
- Use privacy-focused email providers
- Password manager apps are an easy and big win
- VPNs encrypt and anonymize your internet traffic
- Turn on Two-Factor Authentication for sensitive accounts
- Use local encryption on your phone/computer
- Make sure you browse the web via HTTPS
Pay attention to groups like the Electronic Frontier Foundation
Although some of us used to work professionally in digital security, we’re now focused on prepping and don’t publish as neat or detailed stuff as our friends at groups like the EFF. They also build free tools like the popular Privacy Badger browser extension.
So if you want to learn more or keep an eye on this topic over time, consider donating to the EFF and following on social media.
Be prepared. Don’t be a victim.
Want more great content and giveaways? Sign up for The Prepared’s free newsletter and get the best prepping content straight to your inbox. 1-2 emails a month, 0% spam.
The cloud is just other people’s computers
This isn’t so much about a specific widget to buy/install like some of the tips below. It’s more about understanding how things work so you can make smarter decisions.
The thing to keep in mind is that the cloud is simply computers you don’t control. When you take a picture on your phone and Google Photos, iCloud, or Dropbox automatically syncs that photo up to your account, that picture file exists in two places: your phone’s memory and in the computers owned by those companies.
We use the cloud every day and it’s a prerequisite for much of the neat stuff we want in modern life. Just be smart about it.
Plain text messaging is horribly unsafe — use Signal instead
SMS is the basic texting protocol that’s been around since 1990’s cell phones. It’s horrible and you should try to never use it.
There are messaging apps for phones and computers that are free, great to use, fully encrypted, and trustworthy. They don’t sell your data. They can’t even read your data, so the government or hackers can’t access it.
Signal is the king, recommended by Edward Snowden as the best app in the space. The founder of WhatsApp left his own company over privacy concerns (now that WhatsApp is owned by Facebook) and now sits on the board of Signal.
Get Signal for Android, iOS, PC, Mac, or Linux
Sometimes the people you want to communicate with are stubbornly locked into another ecosystem. If you can’t do Signal but still have some choice, favor:
Normal phone and video calls are insecure — use Signal instead
Bonus! Not only is Signal better at the normal messaging app stuff like texting, images, and recorded audio and video, but you can do real-time voice and video calls through the app that are entirely encrypted.
So yeah, go use Signal and even donate to the non-profit that builds/runs it.
Here’s advanced tips on getting the most from Signal, such as setting up PINs to prevent SIM swap attacks.
Other decent video services are:
Use physical barriers to cover cameras
Do you want to rely on the word of companies/governments who’ve already shown they break this trust?

If not, the best way to avoid relying on their goodwill is to physically block lenses. We use these cheap but nice slides on laptop cameras, for example, and there are thinner sticker alternatives if the slide prevents your laptop from closing.
Same theory goes for other things like microphones, eg. this device plugs into a 3.5mm headphone jack, preventing a computer from using a built-in mic to listen.
As consumers, we hope more major companies offer physical kill switches so that we know the device can not be turned on — rather than trusting it won’t be turned on. These must be tangible interruptions in the hardware (ie. the electricity is cut to the camera), not software solutions that can be hacked.
In the meantime, check out smaller privacy-focused companies like System76, which builds laptops and desktops with those tangible kill switches.
Switch to more privacy-focused internet browsers
Browsers like Chrome or Edge are made by hugely-profitable companies with an incentive to track you and make money from your data. Even if their motives are good, there are plenty of examples where a government or hacker could get access to that data.
So, in yet another example of “they can’t steal/spy what they can’t see,” you can better protect this weak point in your chain by using internet browsers that do a better job of respecting privacy.
The current winner is Brave, which is actually based on the same open-source stem cell as Google Chrome, but split off from the roots to craft something different that will still feel the same to you — you can even use all your Chrome extensions in Brave, for example. Here’s more on the topic.
Tip: Although it’s not a silver bullet, more browsers are including privacy settings you can control, such as “do not track” options. Instructions for Brave/Chrome/Chromium, Firefox, Microsoft Edge.
Block trackers with browser plugins
Sometimes called ad blockers, but an ad itself isn’t really a security threat, so we think more about the bad stuff like URLs that try to hijack your browser or install malware.
The top free products in this market are:
Ironic editor’s note: Cookies / “trackers” can be good, too. Sites like The Prepared depend on cookies for affiliate commissions, so that when you click on something we recommend and buy it from a store like REI, the cookie is what tells REI to give TP some credit. Or maybe the site is free and the only way they can support themselves is via ads. You can “whitelist” sites like TP in your plugins so that the plugin knows we’re safe (since we don’t do any actual bad stuff like tracking, data sales, etc.)
Switch to more privacy-focused email providers
Again, companies like Google and Yahoo offer free email services in part to get and monetize your data. And those companies cooperate when governments want surveillance.
Unlike Gmail, services like Proton Mail — the king of this market — are built to respect your privacy both in-house and by not handing data over to governments. Proton is based in Switzerland and the emails are encrypted (at least in part, as it depends who’s on the other end of your email). And it’s free!
This explains Proton vs. services like Gmail.
So if a government like the US wanted to spy on you, it’d be hard for them to compel Proton to comply — and even if Proton did, there isn’t much data to hand over.
Tip: If you ever want to talk to us privately, one way is to use Proton to email us at theprepared-AT-protonmail.com. That way you know it never touched Google&Co’s servers.
Use a password manager to make stronger passwords you don’t have to remember
The most popular password managers:
The vast majority of “hacking” is simply guessing or stealing someone else’s password. Even in really large cases where a government or company was “hacked”, it usually means someone somewhere made a human (not technical) mistake and a third-party was able to gain access. The Equifax and Linkedin breaches are examples of this.
Obviously a password like JHlkt82!!dj29@ is harder for an algorithm to brute-force guess vs. simple passwords or a 9-digit SSN. Even if a service doesn’t have those kinds of “must have” password rules, it’s worth making your passwords as complicated as possible.
But a complicated password isn’t enough — the best way to protect your accounts is by making a complicated password that is unique for each login you have.
Hackers know that most people reuse the same passwords across services. So if the hacker can steal your password from one place, it’s likely they can use that same login info at other services and it will work.
The hacker might not even know what other accounts you have. But armed with an email address and password, their bots can just try logging into all the major things out there (email services, Amazon, Venmo, etc.) until something works.
Password managers are free or cheap programs (eg. $20/yr), usually plug-ins that work right within your web browser. You have one master password — the only one you have to remember. The manager then creates and remembers complicated passwords for each of your accounts. So when you go to log in to PayPal, for example, you put your master password into the manager to unlock it, and then it tells PayPal the unique complicated password.
VPNs shield your data as it moves across the web
A friend who works in high-level tech spying for the CIA said: “The best thing normal people can do is use a VPN. That’s all there is to it. We can beat it if we want to, but it’s a PITA enough that we just move on.”
Imagine sending a postcard through the mail. The post office and mailperson can see who sent it, where it’s going, and what the message is. That’s equivalent to how you use the internet from your phone, desktop, PlayStation, Nest camera, etc. The “postal service” is your ISP (eg. Comcast, AT&T) plus all the other networks and servers in the literal web, while the “mail” is data packets going back and forth through that web.
You might not like that the ‘post office’ can see that stuff at an official level. Or that rogue employees look where they shouldn’t. Or that a government forces the carrier to hand over that private info. Or a hacker gets to it.
A Virtual Private Network (VPN) solves a lot of those problems. It’s a third-party service/software that sits in between you and the open internet. When your computer sends data to the internet, it’s encrypted and goes first to the VPN’s servers. The mail is then repackaged, hiding who the original sender is, and sent out to the final destination.
So even though a company like Comcast owns the wires carrying the data, what they (and the governments tapping into them) can extract from it is much more limited.
They’ve been around a while, but used to be too technical for most people. They’ve gotten easier, and thus more popular — thanks in part to the growing evidence of just how important digital privacy is.
This obviously depends on trusting the VPN. You wouldn’t want to hire the neighborhood gossip queen to be your trusted confidential messenger.
It also depends on where the VPN is located and how they’re set up (eg. they don’t keep traffic logs in the first place). Any company in a country like the US can be strong armed into giving over user data to a government (TK see Texas example). Sure, criminal organisations wouldn’t abide, but you don’t want to use a criminal org. This is why many VPNs are located in countries like Switzerland.
Unfortunately this market is littered with junky services, unethical marketing, and difficulty knowing who’s good or bad. You can’t trust most reviews. At minimum, look for services that never keep logs and are either open source or go through third-party verification (so you know it’s been vetted as legit.)
Do not use a free VPN (unless it’s a limited free trial for a paid plan) — it’s free because they sell your data!
Based on recent reviews, the best VPN services for preppers are:
You can check for updates on these two unbiased review sites here and here.
Turn on Two-Factor Authentication (2FA) to protect your most sensitive accounts
Imagine you normally log in to Google from a Windows laptop in Kansas. Google’s security system knows this pattern. So if there’s a random attempt from an iPhone in China, Google’s algorithm can flag that as suspicious.
If you’ve turned on 2FA in your Google account, when Google notices that unusual behavior, it will send an alert to your mobile phone asking “we just noticed this, is it you?” Thus logging in requires two different authentications.
The idea is that even if a hacker got your password, they don’t have access to your physical phone or phone number, thus they only have one of the two keys.
The second key can take different forms. Sometimes it’s a text message with a code, sometimes it’s a Yes or No button. The more modern approach is to use something like the Google Authenticator mobile app. When you log in to a service and it triggers 2FA, you open the app on your phone and get the temporary 6-digit security code:
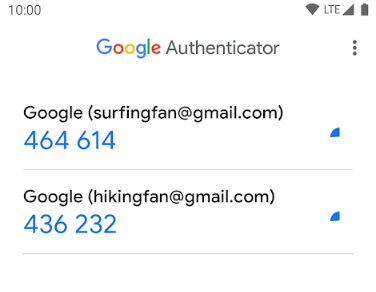
2FA is not yet offered in as many places as it should be, but it’s spreading fast. Most financial and email accounts offer it now. Search the help/FAQ for a service or check the site 2fa.directory to see what services offer 2FA.
Instructions for Google, Facebook, Apple, Microsoft, Yahoo, Amazon
Use local encryption for your phone or computer files
Even with how much is moving to the cloud, you still have local copies of files on your devices, such as the pictures or emails on your phone.
Imagine you get stopped by border security on a holiday. They can plug your phone into a program that copies all of its files. If those files are encrypted, then the oppressor is out of luck.
Thankfully, consumer tech companies have made this easier in recent years. You often don’t even realize it’s turned on, as it just works quietly in the background. Be sure to write down any master passwords (that unlock the encryption) and put it somewhere safe.
Instructions for macOS FileVault, iOS, Windows Bitlocker, Android, Samsung Knox, Veracrypt
Make sure you’re browsing secure websites via HTTPS instead of the old HTTP
Similar to VPNs, this topic deals with protecting your data as it moves across the web when interacting with websites. The added “S” stands for secure. A common example is when you put your credit card info into a smaller e-commerce site — you want that data transmitted over HTTPS.
This is a well-documented topic, so check out this, this, and this.
Some web browsers are building this in by default, such as Firefox.
If your browser doesn’t support this, there are extensions like HTTPS Everywhere (from the Electronic Frontier Foundation) that fill the gap.
